Over the years, research have shown that the Linux operating system which is based on UNIX(the ancestors of Linux operating systems) has been preferred by most users over other operating systems due to its great performance and other notable features.
Speaking of notable features, when it comes to privacy and security, the Linux operating system is one of the best operating systems, however, it is still prone to some security threats. The Linux OS is a multi-user operating system(several users accessing one configured environment of the OS on a particular system), this poses a security threat as it leaves your data at stake if proper file permissions are not put in place. You can imagine what a user with bad intentions can do if he gets access to crucial files, but not to worry, in this article, we would be looking at what file ownership and permissions are all about and how to properly use them to secure our data.
The security feature of authorization in Linux OS is defined in two ways; File ownership and file permissions.
Note: Commands on Linux OS are case sensitive and as such all commands in this article would be written in lower case.
LINUX FILE OWNERSHIP
Before we begin the demo part of how to change file ownership, let us first understand the kind of users on Linux.
In Linux, files and directories are assigned to users. Linux has three different types of users.
- User: This user is also called owner because he/ she originally created the file. This user is denoted by "u".
- Group-users: The group contains different users on the Linux OS that were put together in a group. They are denoted by "g". Note: All users in a group has the same kind of permission access to a file.
- Other users: This refers to every other user who are not creators of any file and who do not belong to any group but has access to your Linux OS. They are denoted by "o".
HOW TO CHANGE FILE OWNERSHIP
To change file ownership, we would make use of the "chown" (change ownership) command.
NOTE: Admins/root users on Linux, has access to every file and directory on the system. To change file ownership, you need administrative/root priviledges.
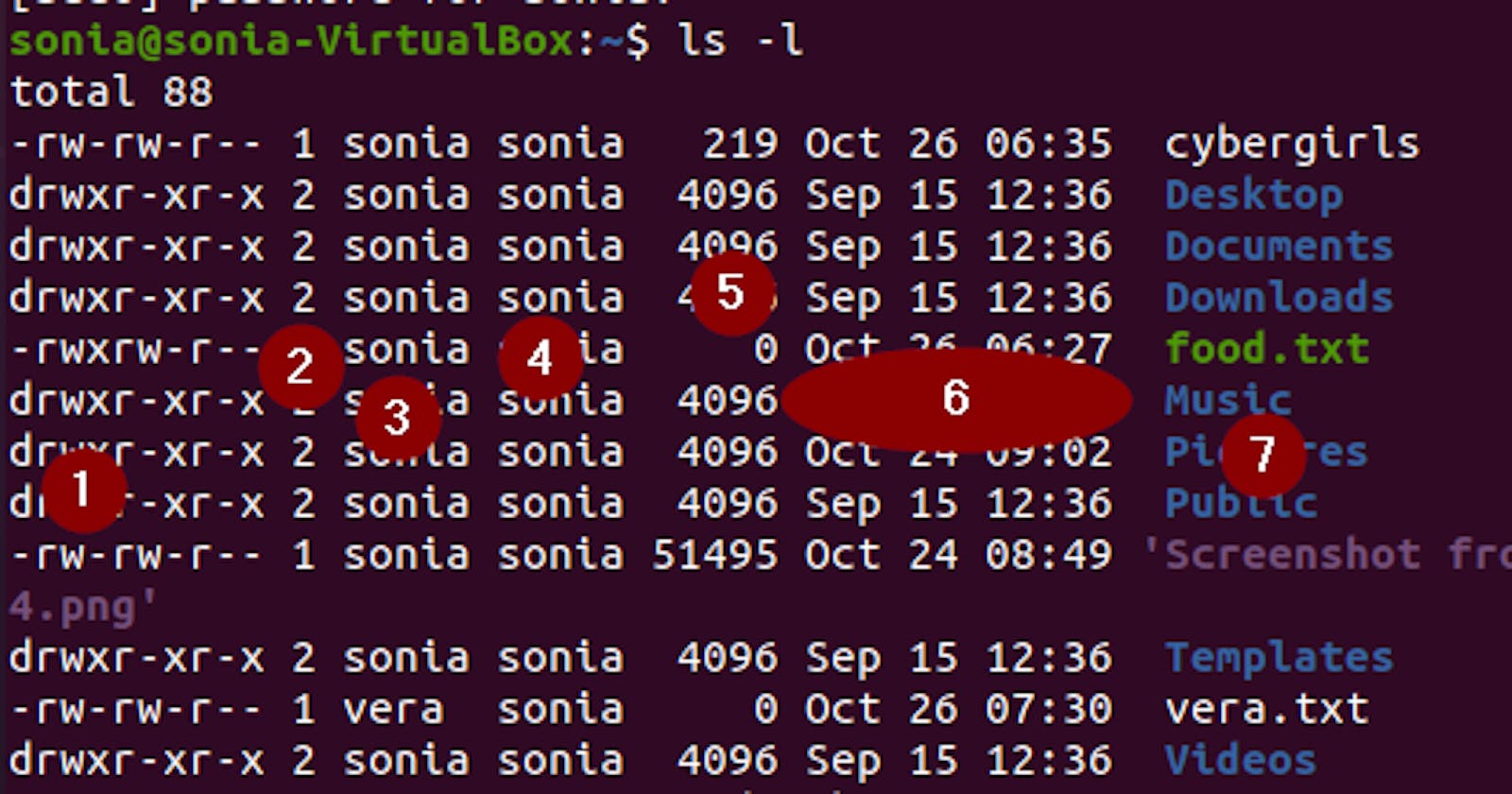
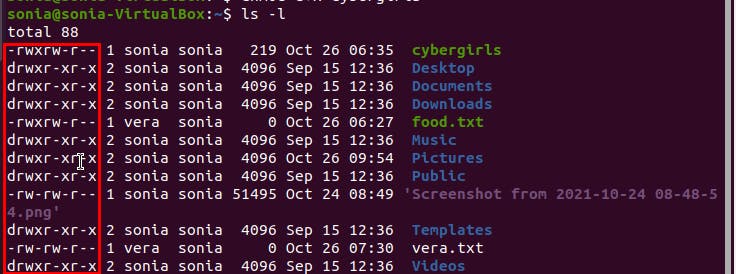
First, let's use the ls command with -l option(ls -l) to view the long list of available files on the system.
 From the image above, we can see that the output of that command gave us a whole lot of information about the files on the system. These pieces of information are further explained below;
From the image above, we can see that the output of that command gave us a whole lot of information about the files on the system. These pieces of information are further explained below;
1- The column labelled 1 shows us the permissions that various users have on the file. This would be explained in detail later in this article.
2- The number of links that the file/directory has.
3- Name of user.
4- Name of the group which the user belongs to.
5- The size of the file(measured in bytes). Tip: use ls -h to view the sizes of the file in a more readable form.
6- The date and time of last modification on that file.
7- Name of file/directory.
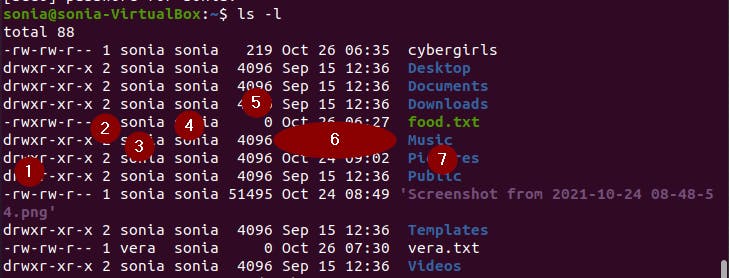
From the image above, we could see different files and the owners of the files e.g the file "food.txt" belongs to the user "sonia".
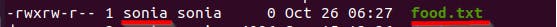 Now what if I wanted to change the ownership of this file from the user "sonia" to another user, let's say user "vera", How do I do this, you may ask? It's easy:
Now what if I wanted to change the ownership of this file from the user "sonia" to another user, let's say user "vera", How do I do this, you may ask? It's easy:
Step 1: Make use of "chown" command but with "sudo" to get root priviledges (sudo chown "name of new user/owner" "name of file").
Step 2: Enter password for root user.
Step 3: Use ls -l to see the changes made. 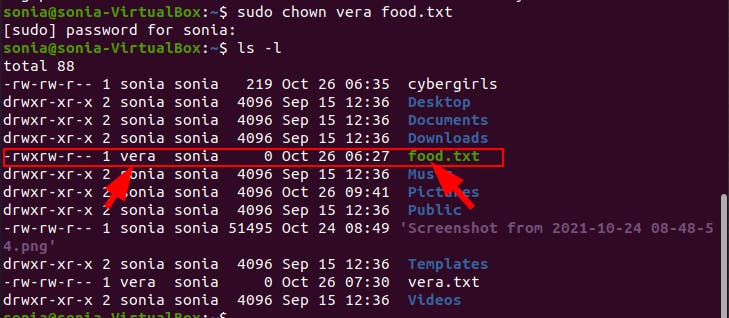 Easy right, now its your turn, go try it!
Easy right, now its your turn, go try it!
LINUX FILE PERMISSIONS
What are file permissions? Simply put, file permissions on Linux defines what kind of access a user has on a file(what a user can and cannot do with a file). The Linux file permissions are divided into three parts;
Read permission(r): With this permission, a user can only read the file but cannot make any change to the file. The read permission is denoted by "r"
Writable permission(w): This permission allows the user to read and write to the file(modify the file) but they cannot execute it.
Executable permission(x): The executable permission allows users to execute a file as though it was a program.
 The above snapshot shows us the permissions that various users on the system has on the files. To view this on your system, use the ls -l command.
The above snapshot shows us the permissions that various users on the system has on the files. To view this on your system, use the ls -l command.
Using the first line of the listed files, the user's permissions on the file "cybergirls" are explained below;
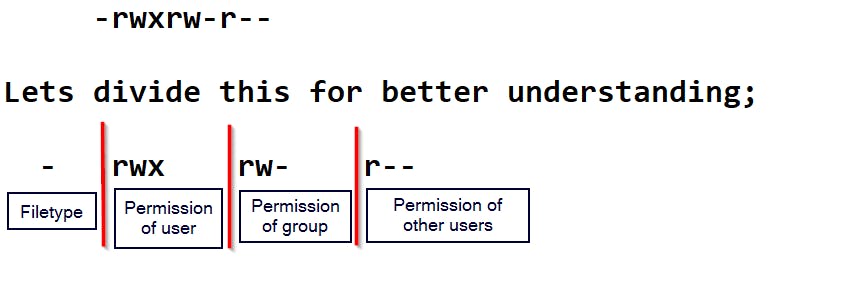 ~the first section(-) tells us what kind of file it is. In the case of the above snapshot, it is just a normal file which is indicated by "-".
~the first section(-) tells us what kind of file it is. In the case of the above snapshot, it is just a normal file which is indicated by "-".
- If it was a directory, it would be indicated by "d".
- If it was a link, it would be indicated by "l".
~The second section(rwx) tells us what permissions the user/owner has on the file. From the snapshot, the user has rwx permissions on the file.
Recall: the readable permission is denoted by "r" , writable permission is denoted by "w" and executable permission is denoted by "x".
Therefore, the user has permissions to read the file(r), write/modify the file (w) and execute the file(x).
~The third part(rw-) tells us the permission of all group_users. Here, the users in the group has just the read(r) and write(w) permissions. The "-" after the r and w permissions shows that the last permission which is supposed to be executable permission is not allowed for the group users Recall that, all users in a group has the same file permission.
~ the fourth part(r--) tells us that the other users who are not the owners of the file and who do not belong to any group on the system has just the read permission and not the write or executable permission.
CHANGING FILE PERMISSIONS
File permissions can be changed making use of the "chmod" command. Note: Only the owners of a file and superuser can change permissions on a file.
There are two ways to changing file permissions; the symbolic and absolute mode.
THE SYMBOLIC MODE: Here, file permissions are changed by the combining letters and symbols. To do this, pick the user you want to change permissions for(Recall that user/owner-"u", group-"g" and the other users are denoted by "o".) and then use the "+" symbol to add permission and the "-" symbol to remove permissions. Let's see this in action;
Adding of permission
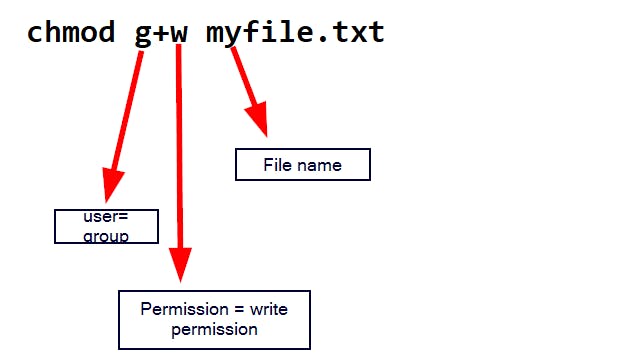 The command in the snapshot above changed the file permission of the group(g) by adding(+) writable permission(w) to the group. So now, the group users have the permission to modify that file. Try this on your own and use ls -l to view the changes made.
The command in the snapshot above changed the file permission of the group(g) by adding(+) writable permission(w) to the group. So now, the group users have the permission to modify that file. Try this on your own and use ls -l to view the changes made.
Removing permissions
 Guess what that command would do. You're absolutely right, it removed the read(r) permission from the other user(o) on myfile.txt.
Guess what that command would do. You're absolutely right, it removed the read(r) permission from the other user(o) on myfile.txt.
You can also set multiple permissions for different users at once. For instance, if I wanted to add the write(w) permission for both the user and group, I'll simply use this command;
 Now both the user and the group has write permission on that file.
Tip: If you want to change permissions for all users(u,g and o) at the same time, you can simply use "all" which is denoted by "a" to specify all users. E.g chmod a+r (this would give all the users read permission).
Now both the user and the group has write permission on that file.
Tip: If you want to change permissions for all users(u,g and o) at the same time, you can simply use "all" which is denoted by "a" to specify all users. E.g chmod a+r (this would give all the users read permission).
- ABSOLUTE(NUMERIC) MODE: In this method, file permissions are changed using numerical representations. This method is a lot more easier than the symbolic mode because it allows you to change permissions for all users at users at once without having to specify u,g or o and without having to use r,w and x like in the symbolic mode, but it's a little bit tricky, so you might want to consider paying absolute attention at this point.
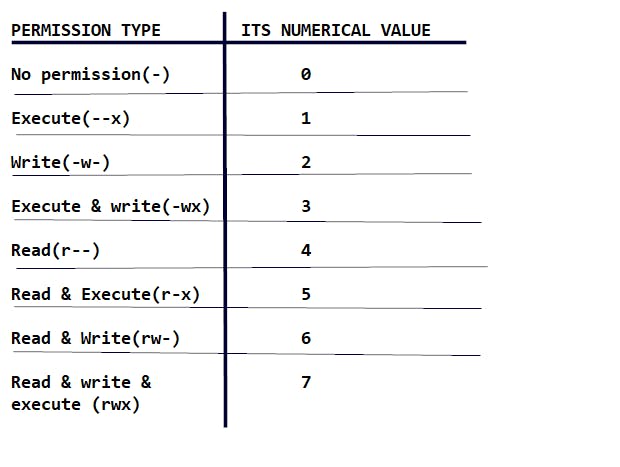
File permissions are represented by numbers in the absolute mode, their representations are:
- Read permission = 4
- Write permission = 2
- Execute permission = 1
Let's take a look at an example;
 In absolute mode, each number represents the permission that each user has. In the example above, the first number(1) represent the permission given to the user/owner, the second number(1) represents the permission of the group and the third number(4) represents the permission of other users. And don't forget, 1=execute, 2=write and 4=read. So from the example, the user has just 1 which is execute permission, the group has just one also which is execute permission and the other users have 4=read permission.
In absolute mode, each number represents the permission that each user has. In the example above, the first number(1) represent the permission given to the user/owner, the second number(1) represents the permission of the group and the third number(4) represents the permission of other users. And don't forget, 1=execute, 2=write and 4=read. So from the example, the user has just 1 which is execute permission, the group has just one also which is execute permission and the other users have 4=read permission.
That was easy, right? Let's take a look another example;
Giving more than one permission to a user; To give a user more than one permission(e.g read and write permission), simply add the numerical values of the permissions together.

In this example, the user/owner was given permission "7", the group-5 and other users-4.....let's break this down;
- user=7 (4_read +2_write +1_execute) , therefore the user has the read, write and execute permission.
- Group=5 (4_read +1_execute), therefore group has the read and execute permission.
- Other users= 4 which means "o" has just read permissions.
The table below shows the permissions and their numerical representations. Make sure to study it.
CONCLUSION
Why set appropriate file permissions? Answer is obvious and simple.... To secure your data!!!
File permissions seems to be an overlooked area of security in many organisations today. Most people think that once they've set a strong password, implemented 2FA etc then they're totally free from any security threat but the truth remains that there is more to staying cybersafe. While file permissions may sound simple, not appropriately setting them could leave room for cyber adversaries in your network.
Insider threats seems to be another growing problem in the cyber space. Recent findings shows that 62% of employees have reported having access to accounts and files that they probably didn't have need for. Insider threats poses a very significant threat to your organisation as it tends to leave your data at stake and can cause more damage than you can imagine. Certain employees who do not need a file shouldn't have access to it. This is called the least priviledge principle.
So while using a strong password, implementing 2FA, not clicking on random links etc, to protect our data, it is also necessary to implement good file permissions across our servers.
Cybersecurity is a must!!! Cyber awareness is a must!!!!! We must leave no stone unturned.... Please share this article, spread the word and educate others.
#Becybersmart